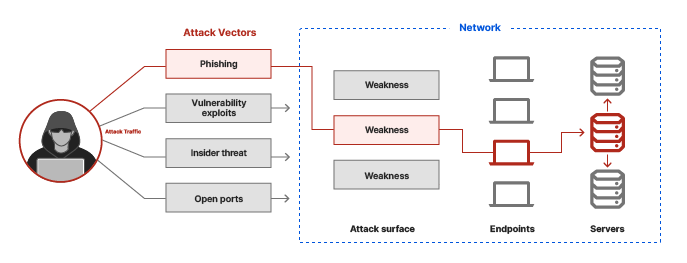
Vector Attack
An attack vector, or threat vector, is a way for attackers to enter a network or system. Common attack vectors include social engineering attacks, credential theft, vulnerability exploits, and insufficient protection against insider threats. A major part of information security is closing off attack vectors whenever possible.
Suppose a security firm is tasked with guarding a rare painting that hangs in a museum. There are a number of ways that a thief could enter and exit the museum — front doors, back doors, elevators, and windows. A thief could enter the museum in some other way too, perhaps by posing as a member of the museum's staff. All of these methods represent attack vectors, and the security firm may try to eliminate them by placing security guards at all doors, putting locks on windows, and regularly screening museum staff to confirm their identity.
Similarly, digital systems all have areas attackers can use as entry points. Because modern computing systems and application environments are so complex, closing off all attack vectors is typically not possible. But strong security practices and safeguards can eliminate most attack vectors, making it far more difficult for attackers to find and use them.
- Cross Cutting Concern
- Deployment Pattern
- Deployment platform
- Access Token
- Communications
- Data consistency
- MACH Architecture
- API-First
- API Marketplace
- Service Mesh
- Loosely Coupled
- On-Premises
- Headless Systems
- Microservices
- Service Template
- Platform-as-a-Service
- u-nat
- Vector Attack
- Candary Deployment
- blue-green
- API fundamentals
- Serverless
- Minimum Viable Product
- Mock Server
- Stakeholders
- Test Server
- Deployment versioning
- Cloud Environment
- API Idea
- Backend for Frontend
- Entry Point
- Strategy
- Refactoring
- Gather Stakeholders Requirements
- Sketch
- Planning
- Research Audience Needs
- Mock Release
- Prototyping
- Feedback from stakeholders
- Git Repository
- Test Release
- Test API
- Main Release
- Microservice Platform
- Cloud Native
- SLA
- Shared plumbing
- Plumbing